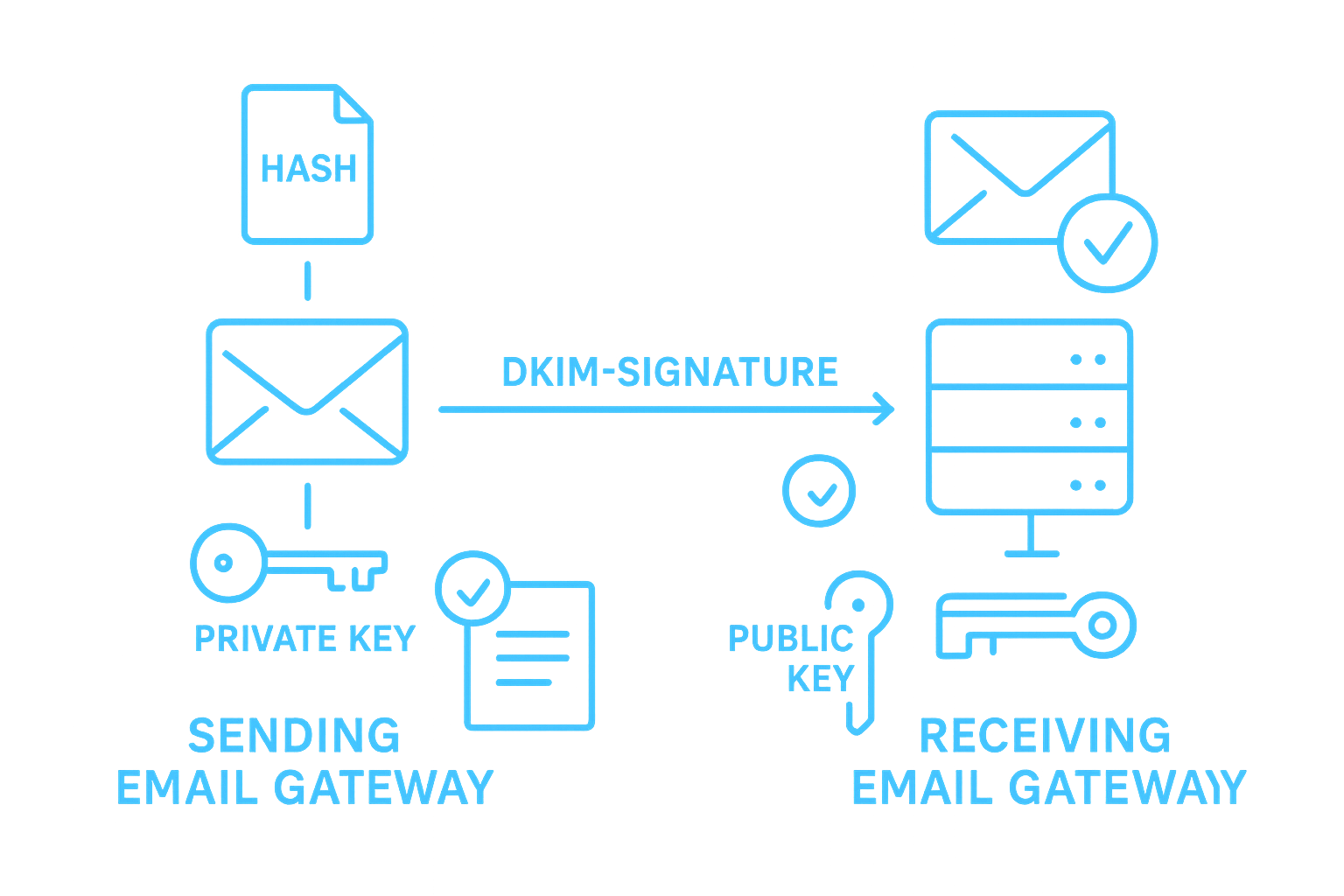
Email Security Frameworks: Why SPF, DKIM, and DMARC Matter
Over the past few years, I’ve helped multiple companies strengthen their email security—both before and after breaches. One thing is clear: Default configurations are not enough—attackers exploit weak setups every day. Protecting your email domain is about safeguarding both your brand and the people who trust your messages. This post summarizes key learnings and practical steps you can take to protect your domain, your users, and others on the internet. Your domain is big part of the company brand and most bussiness still rely strongly on email communication and website.

Keeping your top domain as clean as possible is highly recommended. Letting third-party vendors send from your top domain is risky. If their systems are compromised, attackers can impersonate your brand—and still pass SPF, DKIM, and DMARC checks.
Use dedicated subdomains for vendors (e.g., @vendor.yourdomain.tld) and keep primary identities like
ceo@yourdomain.tld protected. If you are not using the vendor remove the subdomain and thereby all permission to send email with your domain.
 Tip: If a subdomain do not have SPF or DMARC policy, top domain policies will apply.
Tip: If a subdomain do not have SPF or DMARC policy, top domain policies will apply.
Over the past few years, I’ve helped multiple companies strengthen their email security—both before and after breaches. One thing is clear: Default configurations are not enough—attackers exploit weak setups every day. Protecting your email domain is about safeguarding both your brand and the people who trust your messages. This post summarizes key learnings and practical steps you can take to protect your domain, your users, and others on the internet. Your domain is big part of the company brand and most bussiness still rely strongly on email communication and website.

Keeping your top domain as clean as possible is highly recommended. Letting third-party vendors send from your top domain is risky. If their systems are compromised, attackers can impersonate your brand—and still pass SPF, DKIM, and DMARC checks.
Use dedicated subdomains for vendors (e.g., @vendor.yourdomain.tld) and keep primary identities like
ceo@yourdomain.tld protected. If you are not using the vendor remove the subdomain and thereby all permission to send email with your domain.
![]() Tip: If a subdomain do not have SPF or DMARC policy, top domain policies will apply.
Tip: If a subdomain do not have SPF or DMARC policy, top domain policies will apply.